OVERVIEW
In October of 2019, a group of relatively new ransomware strains called Mailto and Mailto-2 were found in the wild. These two ransomware types were also known as “Kokoklock” and “Kazkavkovkiz” where the names have been used interchangeably with no clear definitions at this point of time.
This ransomware group gained attention with the recent ransomware attack against the Australian Toll Group. The Australian Toll Group has subsequently disclosed that their network was being attacked by the Mailto ransomware prior to a service disruption and system shut down.
The Proficio Threat Intelligence Team posted information about Toll Group attacks in our Twitter Feed. In this blog, we share some of our findings pertaining to this new ransomware’s behavior in the wild.
RANSOMWARE DETAILS
This type ransomware is relatively new and first surfaced in late 2019, and as such there is limited information available. Mailto ransomware was seen in the wild during the month of September where Mailto-2 ransomware was seen around October. They are recognizable by the extension that is appended to encrypted victims’ files.
There is some evidence that Mailto actors may have utilized techniques such as phishing and password spray attacks, and then used compromised accounts to send further phishing emails to the users’ address book to spread malware. At this time, there is no known information on the cyber groups that are responsible for these types of ransomware, nor is there information on the C2 activities on them.
Upon successful infection of the victims’ systems, both variants of ransomware include a personal extension on infected files, a ransom note and a readme text file to instruct victims on how to make the ransom payment. The main visible difference between “Mailto / Kokoklock” and “Mailto-2 / Kazkavkovkiz” is the personal extensions appended onto the encrypted file.
At this time, the only other notable information that distinguishes this ransomware strain from others operating in the wild is that the targets are instructed to communicate with the attacker via an email provided in the ransom notes. Ransom notes associated with this ransomware include two email addresses with the email domains “@cock[dot]li” and “@tutanota[dot]com”. “Tutanota” is a free and open-source, end-to-end encrypted email. “Cock[dot]li” appears to be a free anonymous email service also known as “Cockmail”, which has been seen to be used in multiple malicious activities.
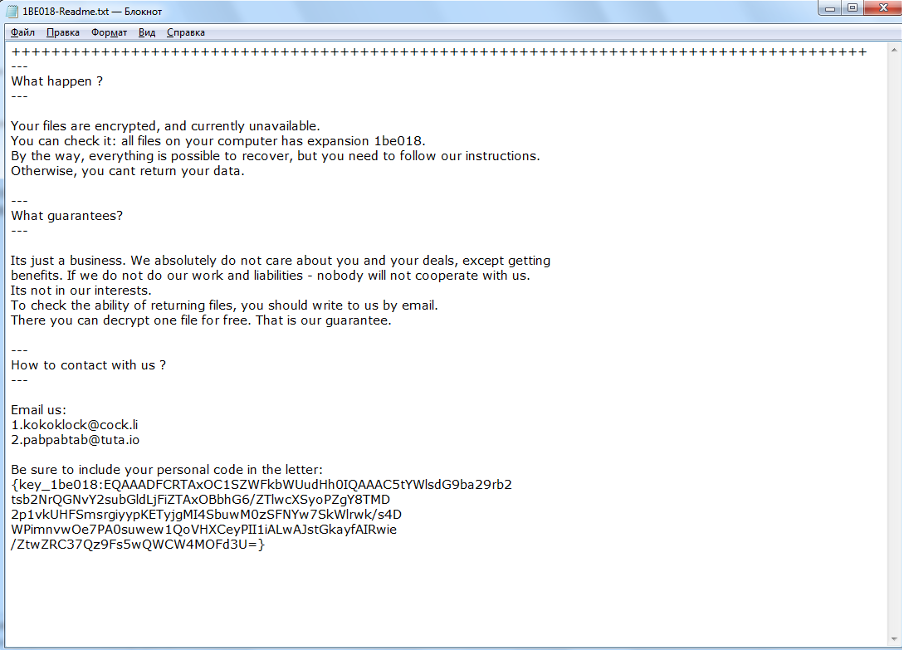
Figure 1 – An example of ransom notes
Beyond the ransom notes, we are also able to differentiate Mailto ransomware based on the file extension appended on the encrypted files. Following the file extension “[dot]mailto”, “Mailto / Kokoklock” ransomware would append six random alphanumerical digits onto the encrypted files while “Mailto-2 / Kazkavkovkiz” ransomware would append four or five random digits onto the encrypted files. While these extensions are the only ones currently seen in the wild, they may vary over time.
Other noticeable differences between both ransomware variants include the following:
| Mailto / Kokoklock | Mailto-2 / Kazkavkovkiz | |
| Decryptor tool | Netwalker | NIL |
| Encryption Method | Suspected Salsa20 Stream Cipher | AES |
| Format of encrypted files | .mailto[<email_address>].<6_alphanumerical_random_digits> | .mailto[<email_address>].<random_digits> |
| Readme file format | <6_alphanumerical_random_digits>-Readme.txt | <random_digits>-Readme.txt |
| Other behaviour | Seen to masquerade as a legitimate program [Sticky password] | NIL |
PRECAUTIONARY MEASURES
Prevention is better than a cure. It is advisable to safeguard your organization to avoid being the next victim of this ransomware attack. We recommend your organization consider the following measures:
- Keep your anti-virus software / EDR solutions and other security tools installed on the systems updated for detection of and prevention from the spread of ransomware.
- Perform regular backups on critical files and systems.
- Keep your operating systems up to date on the latest security patches.
- Make use of network segmentation alongside the zero-trust model.
- Apply content filters on email gateways and email systems to prevent malicious content from reaching users and reduce the chance of a possible compromise.
- Educate your employees and users to improve cybersecurity awareness.
The Proficio Threat Intelligence Team will continue to monitor developments around this this new ransomware and provide updates as applicable.